Do you know the number of concentration risks hiding in your supply chain?
Uncovering concentration risks in the supply chains of investment funds & private equity firms
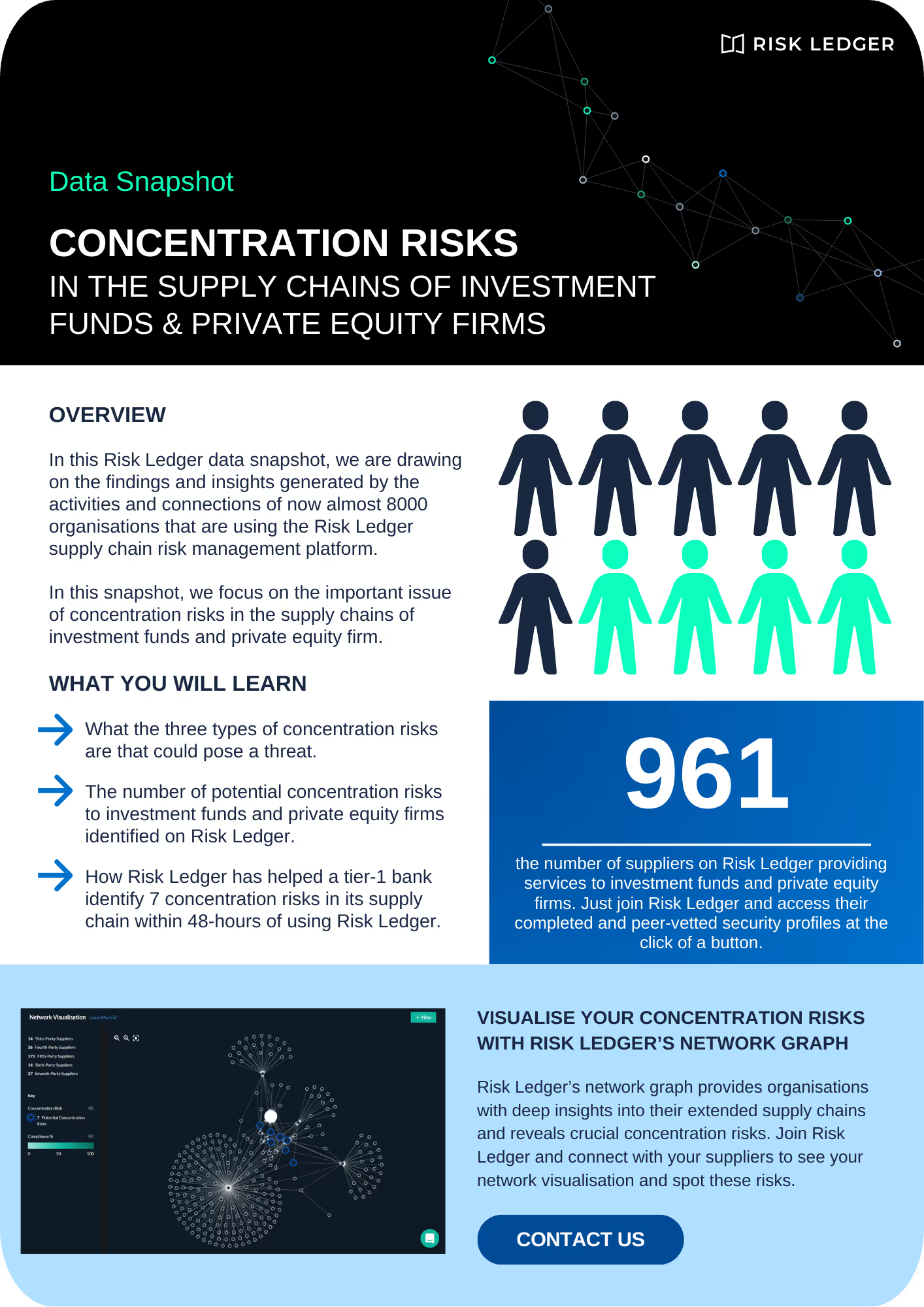
Almost 8000 organisations are already using Risk Ledger's cutting-edge platform for real-time supply chain security, which enables organisations to Defend-as-One because every link matters in cyber security.
Visualising client-supplier networks, Risk Ledger is able to map interdependencies and risks well beyond organisations' immediate third-parties, into 4th, 5th and nth parties. This allows the uncovering of hidden concentration and systemic risks that could pose a threat to the cyber security and operational resilience of organisations and entire industries.
In our recent data snapshot, we identified key concentrations risks for our existing investment fund and private equity clients on our platform.
Do you know which concentration risks might be hiding in your extended supply chains?
If you want to learn more about concentration risks, and how Risk Ledger helps organisations uncover and mitigate them, then download our free data snapshot report.
What you will learn in this data snapshot
Find out what the three types of concentration risks are that could pose a threat to your organisation.
Learn about how Risk Ledger's advanced network visualisation tool is able to identify concentration risks in your supply chain.
Discover how we helped a Tier-1 Bank identify, within 48-hours, all their 3rd, 4th, and nth party suppliers, and, crucially, 7 concentration risks within their supply chain.