
Changelog
New updates and improvements to Risk Ledger

New updates and improvements to Risk Ledger

Meaningful supplier decisions start with data you can trust. That means having a standardised, consistent way to measure supplier performance so you have a clearer picture of whether your suppliers actually meet your security requirements.
This month, we've made compliance scores more accurate and relevant to your security policies.
Compliance scores now reflect what matters most to your organisation, that is, whether your suppliers meet the security requirements you've set.
What's changed
The result is a clearer picture of your supply chain, one that reflects your own policies and gives you a strong basis for supplier decisions, whether you're approving a supplier, escalating a risk, or reporting to the board.
You may notice some scores have shifted as a result of these changes. This is expected, and reflects a more accurate picture of your supply chain.
Learn more about these changes in our Help Centre.
.jpg)
January's updates remove friction from supplier security monitoring. We've automated asset discovery for External Monitoring and refreshed our assessment framework to keep pace with evolving security requirements - no action needed from you.
Previously, External Monitoring only scanned assets that suppliers manually added (typically just their marketing website). But we know that Clients rely on more than their marketing websites to deliver business-critical products and services.
What's new:
Asset Discovery automatically identifies and monitors a supplier's full digital footprint, immediately surfacing security signals across their entire attack surface. Get comprehensive coverage from day one, revealing risks across domains and subdomains that might otherwise remain hidden, without waiting for suppliers to manually build their asset list.
Asset Discovery is automatically enabled for all External Monitoring clients and available to all suppliers.
Learn more about External Monitoring here.
We update our Standardised Assessment Framework every 6 months to maintain relevance with current security standards and regulatory requirements, without you having to do the heavy lifting.
What's changed:
Get details of the changes in our Help Centre.
These changes are now live. Suppliers currently completing their assessments have been notified of the changes. All other suppliers will see these updates at their next reassessment.
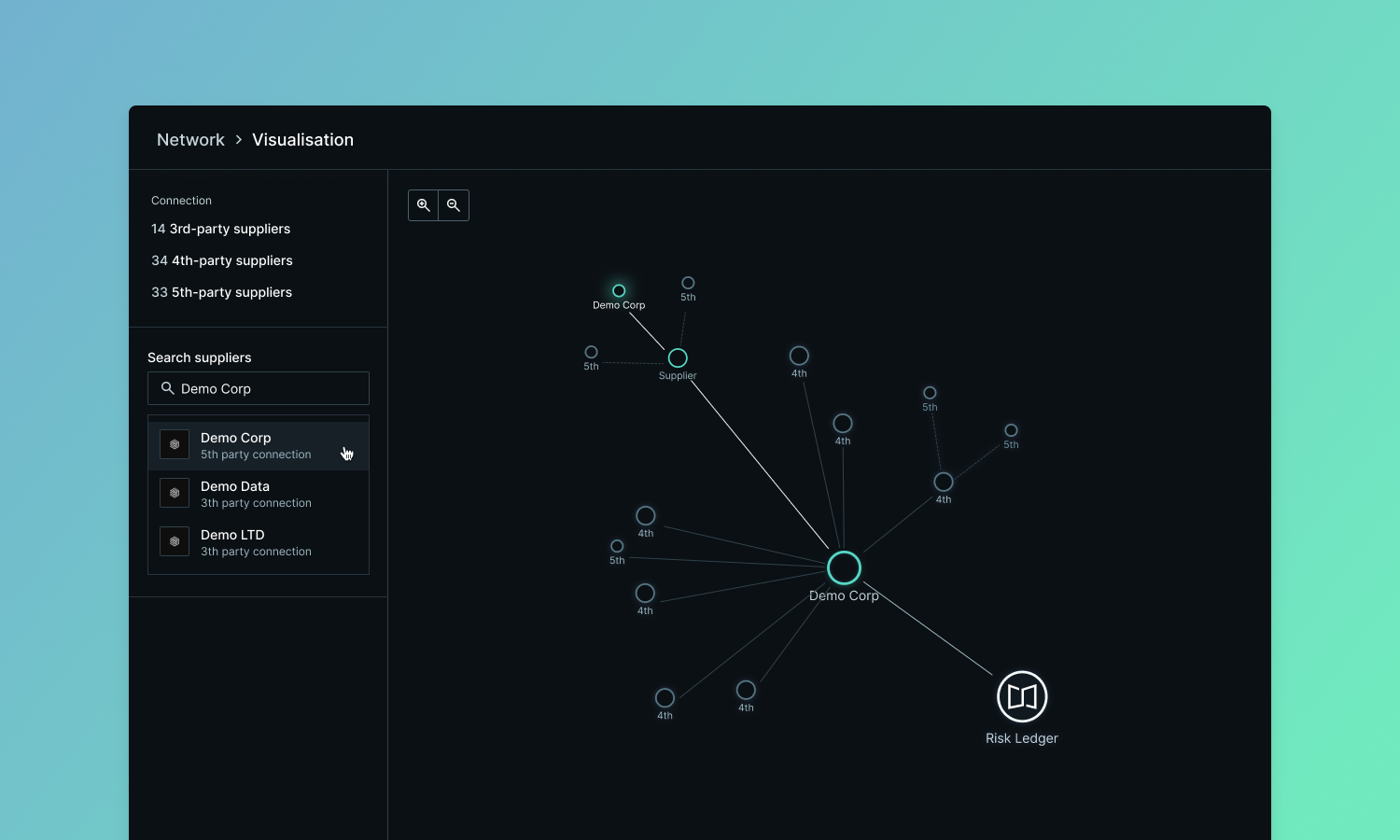
Understanding your supply chain means knowing who delivers critical services, who holds confidential information, and who you share PII with.
This month's updates make it easier to layer these insights onto your network map and get visibility into suppliers earlier in the relationship.
As your supplier network grows in size and complexity, you need better tools to cut through the noise and focus on what matters. We've added new capabilities to help you identify concentration risks and plan for business resilience.
What's new
These capabilities are live in your account and available on both your own map and the community map.
Security teams told us they wanted visibility into suppliers while waiting for connection requests to be accepted. Now you can.
What's new
Clients with External Monitoring can now see scan findings for publicly available domains on both Unclaimed Profiles and Basic Connections (suppliers who haven't yet accepted your connection request).
This means you can start assessing a supplier's external security posture from day one, rather than waiting for them to respond.

Risk Ledger is building a network where Clients and Suppliers connect and collaborate on security together. To make that work, we're constantly improving how connections happen on the platform. Alongside other backend and performance improvements, here's what's new this month.
What’s new:
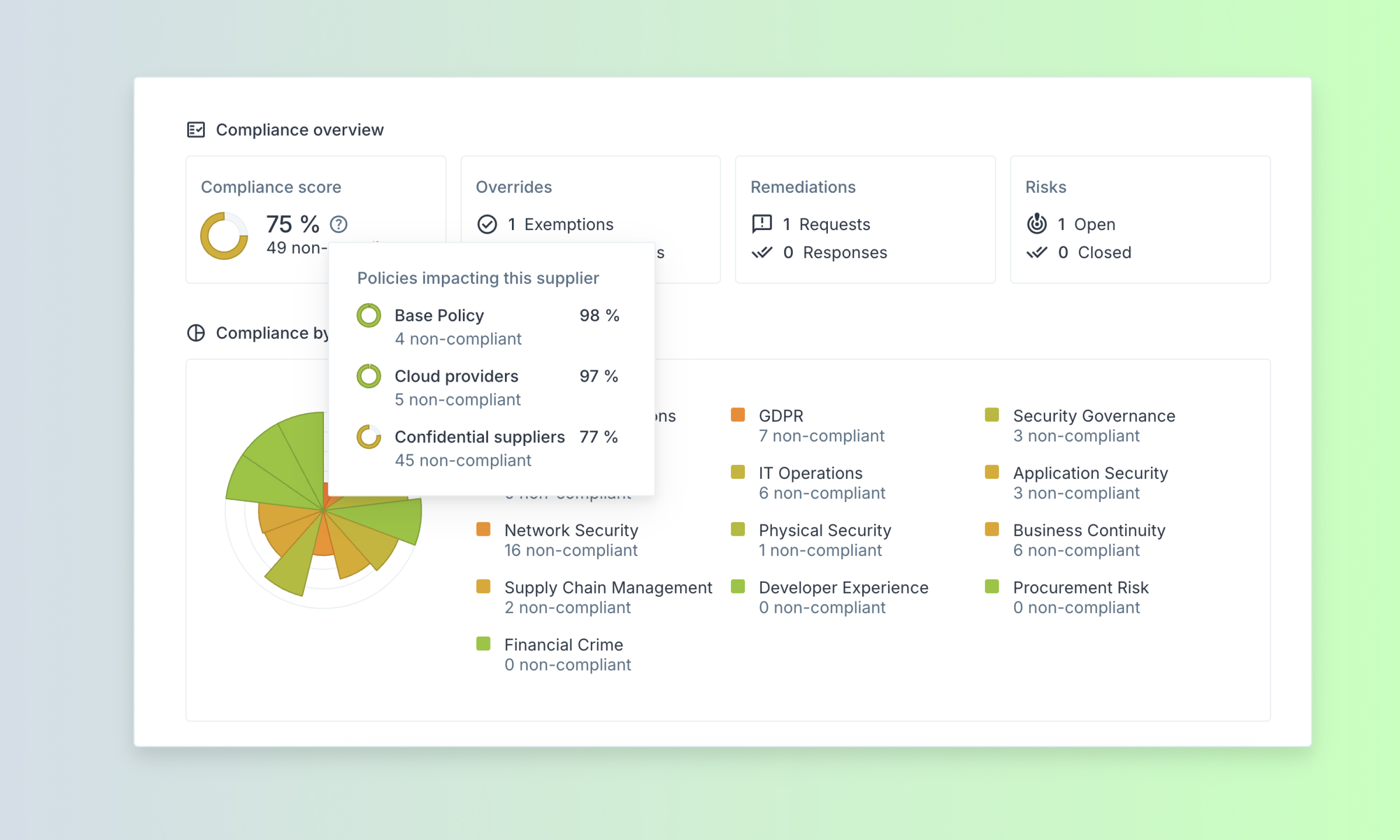
This month's updates are all about transparency and control. You asked for clearer compliance scoring, more flexible permissions, and better connection workflows, so that's exactly what we've built.
Previously, it was unclear which policies and controls applied to each supplier, which slowed reviews as reviewers had to jump between different parts of the platform.
Based on user feedback, we've made it easier to understand how compliance scores are calculated, giving you greater transparency into supplier assessments.
What’s new:
This improvement helps you make faster, more informed decisions about supplier risk by showing exactly how scores are calculated.
Emerging threats helps you quickly assess supply chain impact when critical vulnerabilities or incidents emerge. When we identify a significant threat, suppliers receive a brief questionnaire so you can understand your exposure in hours, not weeks.
Based on your feedback, we've added granular control over who can view emerging threats.
What’s new:
This gives you flexibility to tailor what different teams see. For example, if procurement teams use Risk Ledger, you can hide emerging threats from their view to keep their workflow focused without overwhelming them with supplier security details.
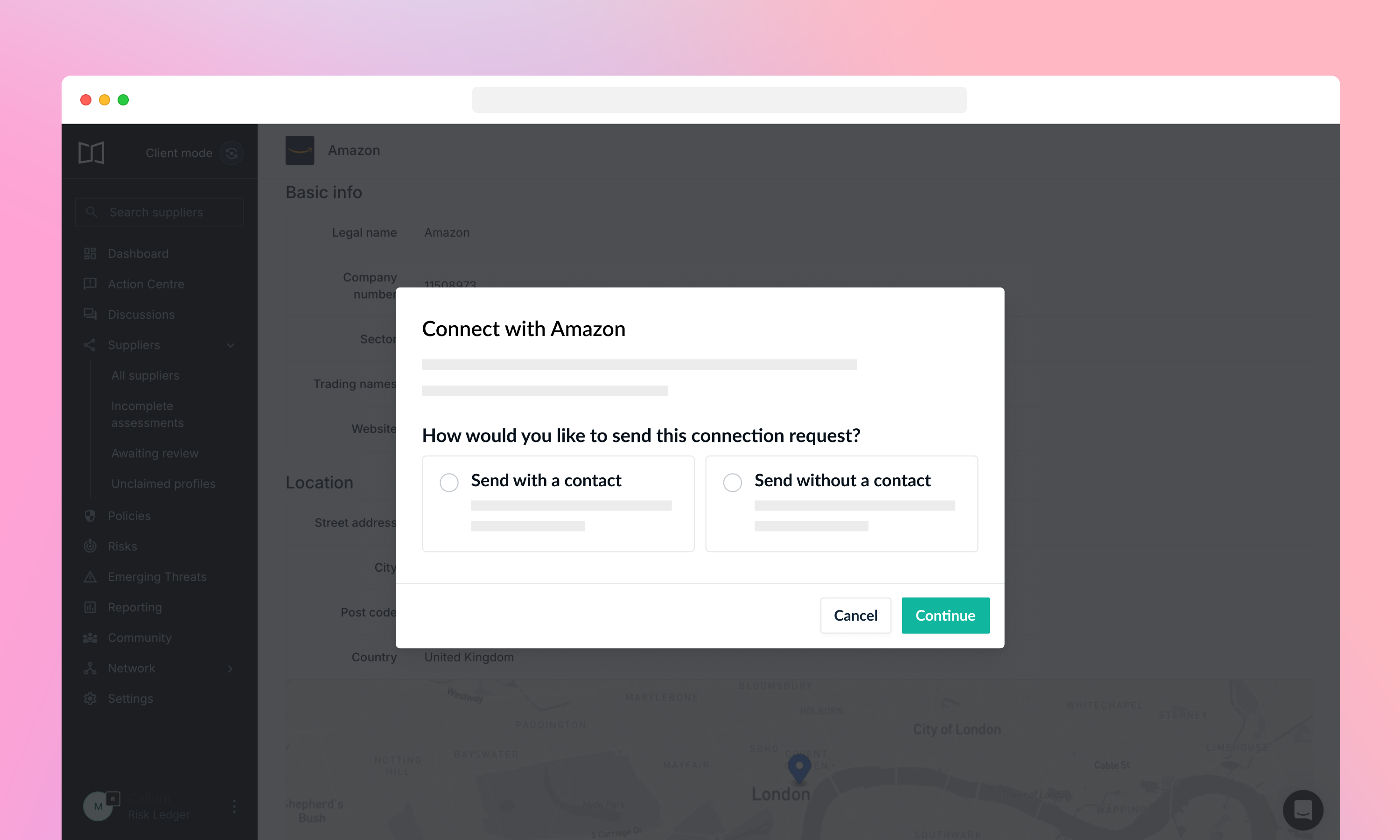
We’ve found that client Connection Requests with supplier contact details are 64% more likely to be accepted.
So, we’ve introduced a prompt for Clients to enter the details of their Supplier point of contact to increase acceptance rates and speed up reviews.
What's new:
When sending a manual connection request, you'll now choose between:
This helps you understand the impact of including contact information while giving you control over your outreach approach.
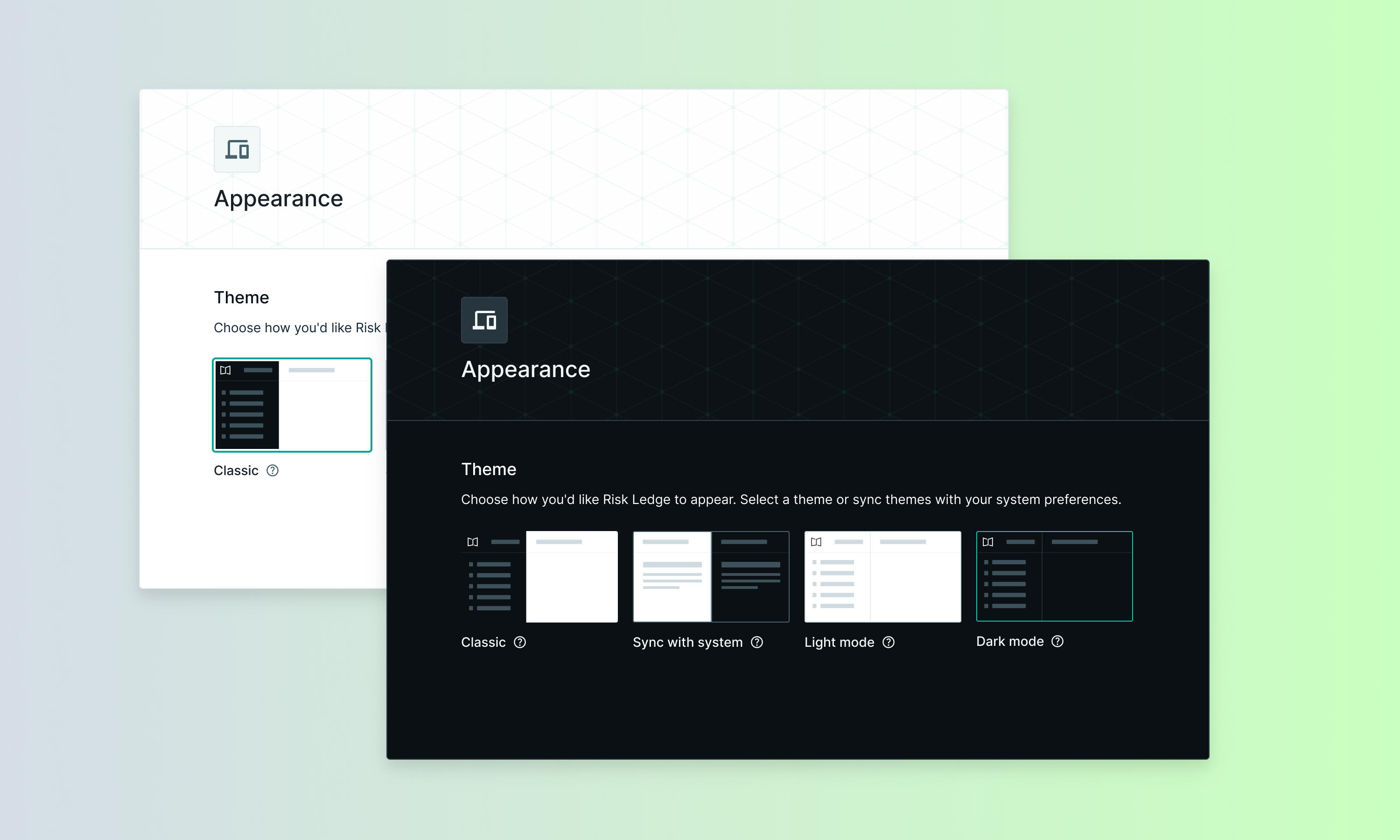
We've added light and dark mode options to improve accessibility and give you more control over your Risk Ledger experience.
Navigate to Settings > Appearance and choose from:
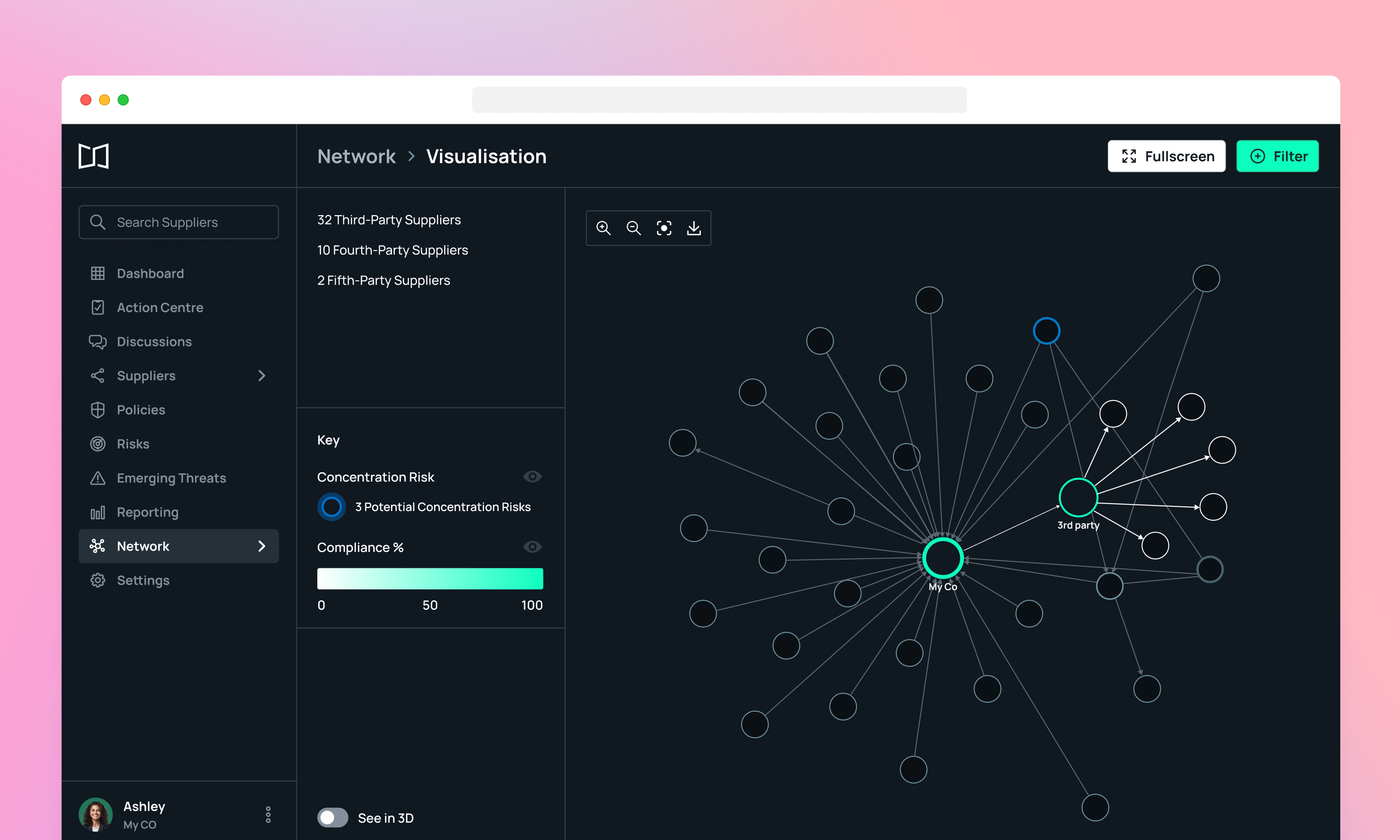
This month brought significant enhancements to how you visualise and understand your extended supply chain.
With the launch of Fourth Parties, you can now map critical dependencies beyond your direct suppliers, whilst our improved Network Visualisation makes it easier to spot concentration risks across complex supplier networks.
We've also refined our assessment framework and enhanced supplier collaboration tools to drive faster, more accurate risk assessments.
Client and supplier relationships are complex and ever-evolving. You need a real-time, comprehensive overview of your suppliers’ suppliers to identify and understand changing critical dependencies and concentration risks.
We launched Fourth Parties to solve this. Clients can get true visibility of their suppliers’ critical suppliers, plotted in our Network Visualisation tool for faster, deeper supply chain analysis.
Here’s how it works:
Fourth Parties is now live on the Risk Ledger Supply Chain Security Platform ready for Clients and Suppliers to explore.
You can learn more about the feature on our blog or in our Help Center.
Along with the launch of Fourth Parties, we continued to enhanced our Network Visualisation tool to ensure it gives businesses a clear and accurate picture of how businesses are connected to one another across multiple tiers of relationships.
What’s changed:
We update our Standardised Assessment Framework every six months to ensure that the framework remains relevant to changing regulatory and business demands, while maintaining consistency for clear comparison.
In our latest update, these are the changes we made:
You can learn more about what this means for Clients here, and Suppliers here.
For Suppliers to complete an assessment, it takes multiple people across different teams to work together. So, we’re improving how Supplier teams collaborate on Risk Ledger with these new features:
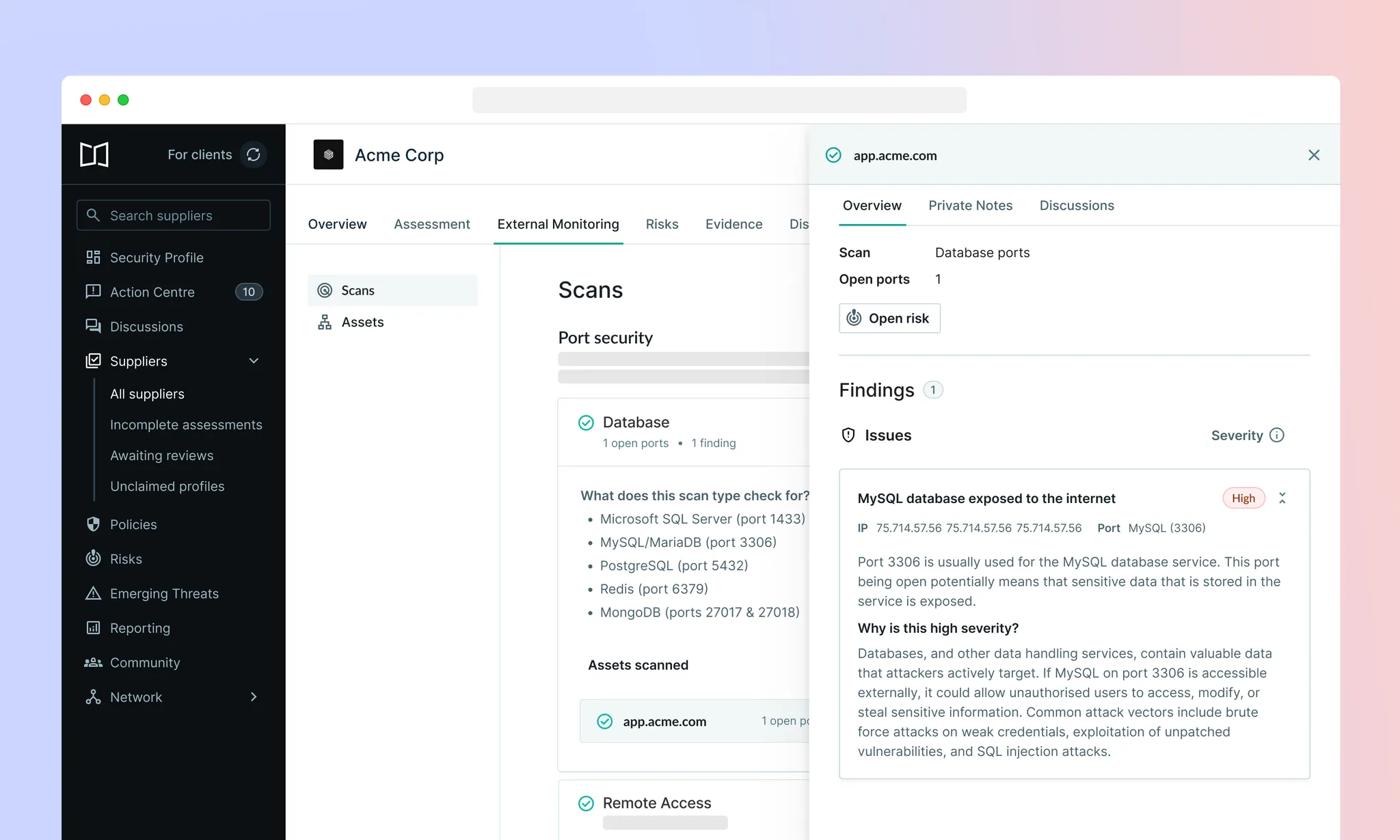
When assessing their suppliers, companies are always looking for ways to verify what suppliers claim to do. With External Monitoring (Beta), we're complementing supplier assessments with external, objective data to verify their security posture.
This month, we're expanding these capabilities with port scanning and enhanced findings navigation.
Port Scanning automatically checks suppliers' digital assets for open ports that are frequently targeted in cyber attacks.
We focus on the most critical vulnerabilities across remote access, databases, web services, file sharing, and infrastructure—reducing noise whilst surfacing the findings that matter most.
Like all External Monitoring features, port scanning results appear directly within your suppliers' profiles alongside their assessment responses, giving you the complete picture without having to jump back and forth between different tools.
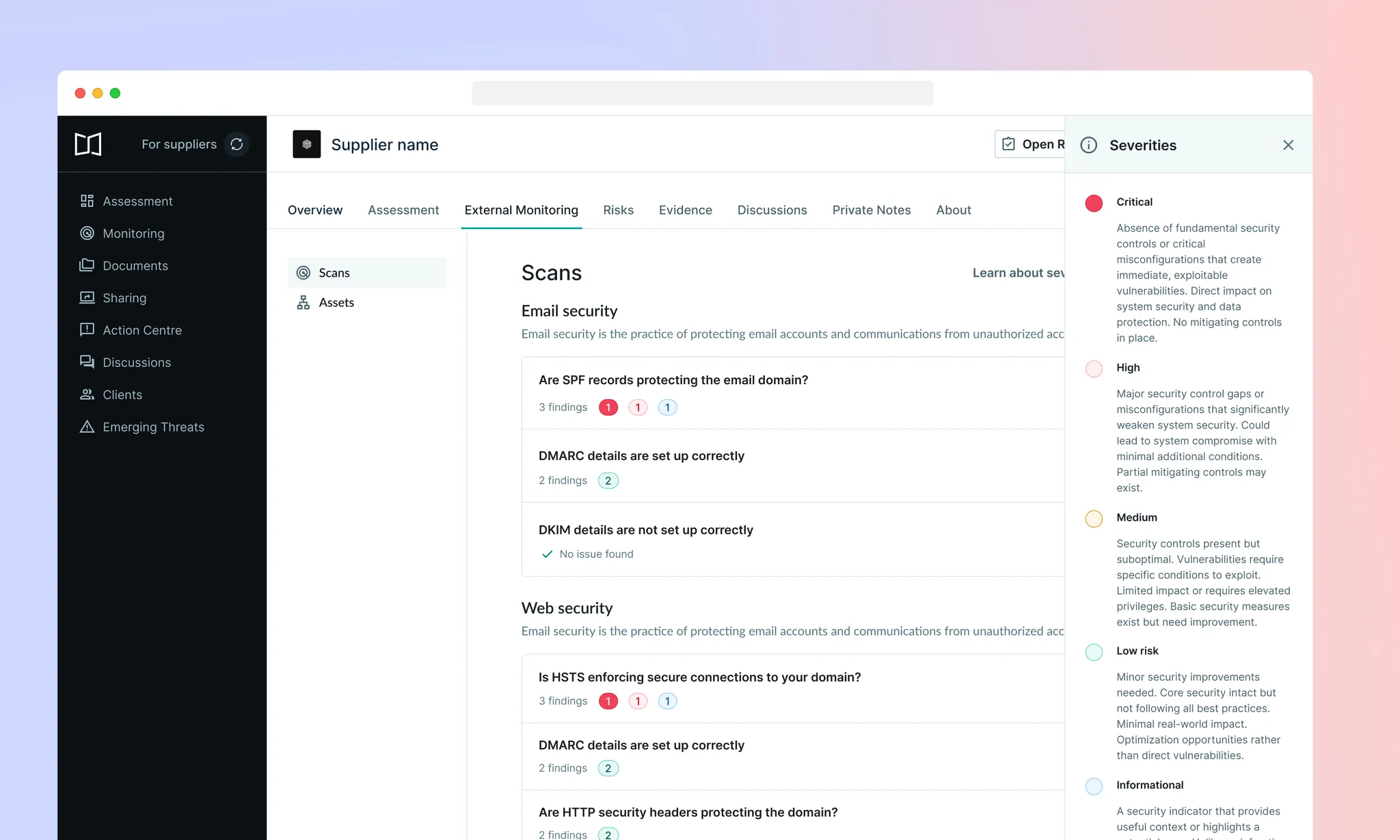
Based on user feedback of early versions of External Monitoring (Beta), we’ve updated our severity indicators and explainers to provide more context and transparency to users about how we assign severity ratings to scan findings.
We’ve introduced two new ways for Clients to quickly view Supplier scans and help prioritise the findings they should be looking at, focussing on critical issues or specific assets.
We’re also simplifying the supplier onboarding flow to speed up assessment completion times. So far, we’ve introduced some design changes to the initial signup flow to make the experience more enjoyable for new users.
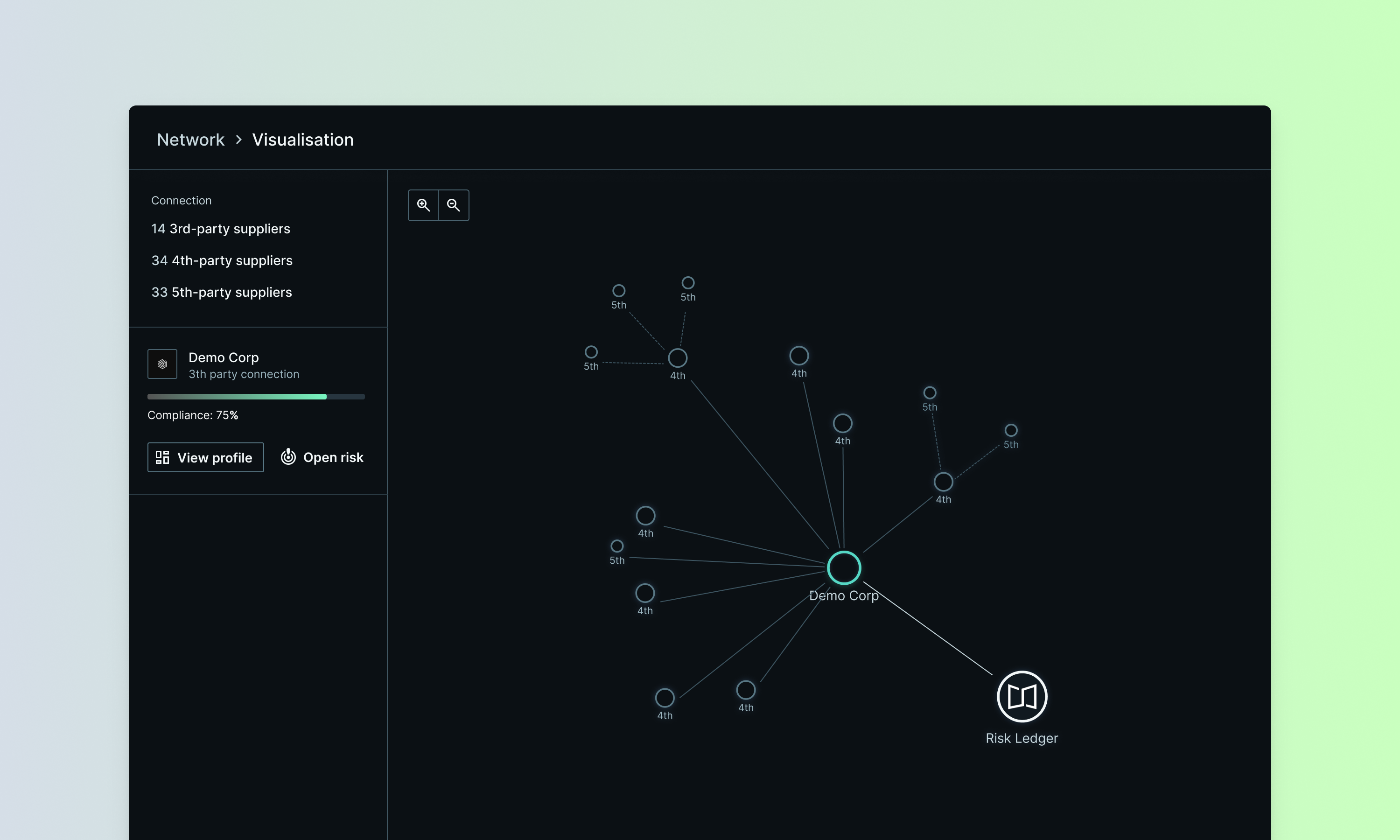
As more organisations join the Risk Ledger network and supply chain maps become increasingly complex, we wanted to ensure our visualisation tools could handle even the most intricate supplier relationships without compromising on performance or clarity.
This month, Network Visualisation got significant performance improvements and enhanced usability, making it easier to see and understand the connections throughout your supply chain, from third parties all the way down to sixth-parties and beyond.
We've overhauled the performance of our network graphs. Whether you're viewing your own supply chain or the most complex, interconnected supplier network, the visualisation now runs smoothly without lag or delays. This improvement ensures that even organisations with extensive nth-party relationships can explore their networks seamlessly.
You can now jump directly to the network visualisation from any Supplier Profile. This new feature provides immediate access to both your supply chain and community network (if you're part of a community), making it easier to understand how each supplier fits within your broader ecosystem.
Better supplier identification: Hover over any node in the network map to quickly see the supplier’s name. Click on each node to explore nth party connections and understand the full relationship chain.
Clearer connection paths: We've made design improvements that make it easier to see how suppliers connect to your organisation, helping you trace relationships and dependencies more effectively.
Compliance score visibility: Nodes now clearly indicate which suppliers have compliance scores and which don't. Green nodes represent suppliers with completed assessments, whilst white nodes help you quickly identify unclaimed profiles, incomplete assessments, or suppliers where policies haven’t been applied yet.
Note: These improvements apply to both your own supply chain graph and the community network map, if you’re part of a community.
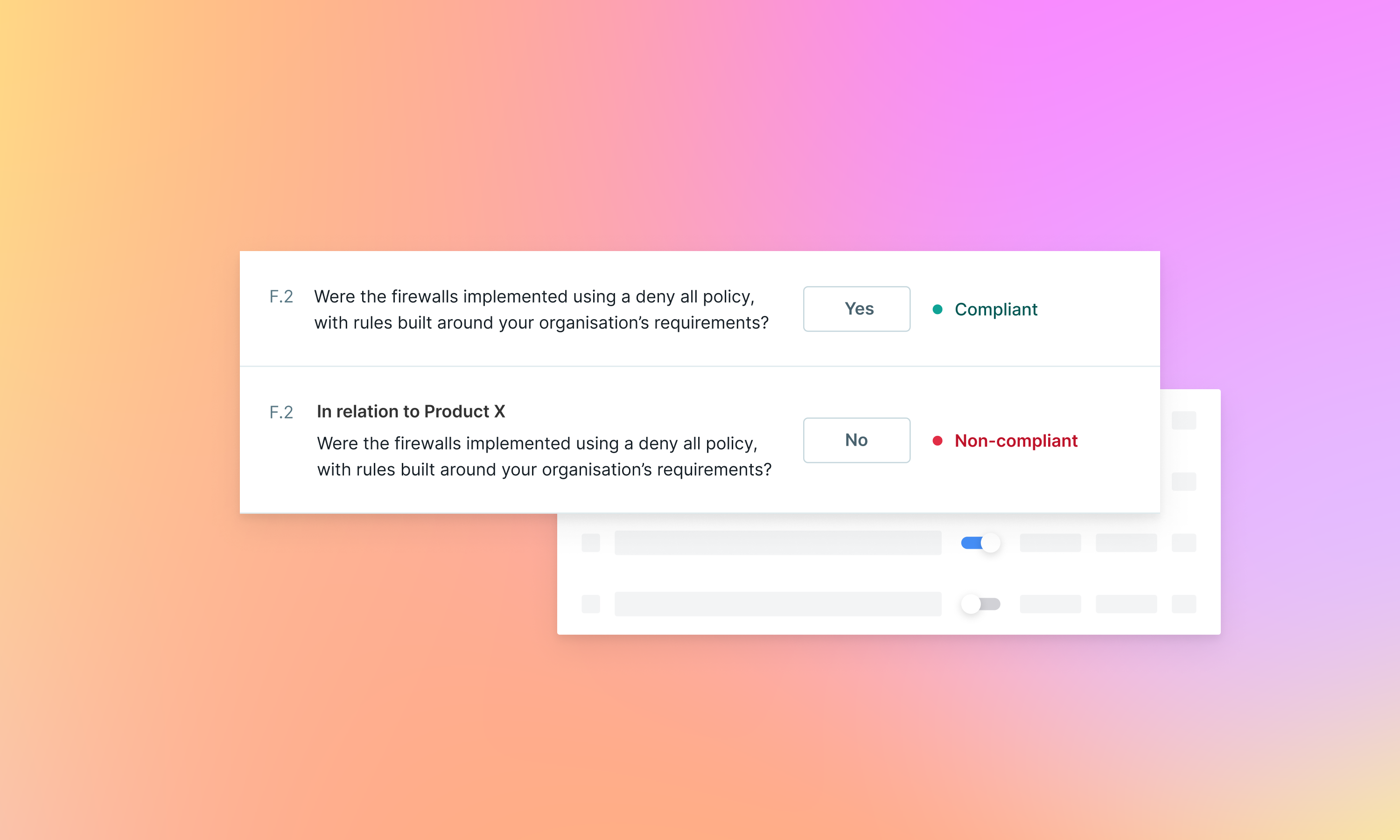
Earlier this month, we launched Product Level Answers, a fundamental update to our assessment that allows suppliers to accurately represent varying security controls across multiple products, within a single profile.
Instead of maintaining separate accounts or duplicating information, suppliers can set organisational-level answers as a baseline and highlight the differences where security controls vary by product. Suppliers can then share precise and relevant information with each client and Clients can clearly identify security control variations across different products, leading to more accurate risk assessments.

While Risk ledger’s full and standardised framework offers a comprehensive assessment of larger and critical suppliers. However, what has become more evident over time that increasing the visibility and coverage of your less critical or smaller suppliers has a compounding effect.
The original full framework with its 192 controls across 10 security domains provides you with the depth and coverage needed to ensure that your larger and more critical suppliers have a strong security posture in place. We have now introduced an additional and lighter version with only 44 control questions to ease the burden on smaller and less critical suppliers. This new configuration method allows flexibility and wider coverage of your supplier network, increasing uptake and engagement from your smaller or less mature suppliers. This is especially beneficial for those suppliers with limited resources, or which are in the earlier stages of developing their security practices.
But flexibility is key. Following this change, you now have the ability to adjust the scope of assessment questions based on your evolving relationship or changes in your suppliers’ risk profiles or your risk appetite. Either increase the assessment if a supplier becomes more critical or high risk, or decrease the assessment scope for smaller or lower-risk suppliers to increase their engagement with your programme.

Want to use Risk Ledger to effortlessly uncover insights and trends across your suppliers? Whether it's identifying which suppliers are compliant with your sustainability criteria or understanding how many of your suppliers hold a security certification, you can do this now with Insights Reporting.

Monthly research, case studies and practical guides you won't find anywhere else.
Join thousands of security managers turning their TPRM programmes into success stories.